What Are Ring Signatures?
A Ring Signature is a digital signature where a transaction is signed on behalf of a group. This makes it computationally impossible to determine which group member generated the signature. Ring signatures are used in privacy-focused cryptocurrencies like Monero to hide the identity of the sender.
Source: HelloFuture
Introduction
Cryptocurrencies have gained widespread adoption due to their ability to provide privacy in financial transactions. This privacy feature can be used for both legitimate and illicit purposes. Ring Signatures, a cryptographic technique, is an important method contributing to this privacy.
Ring Signatures were introduced by Rivest, Shamir and Tauman in 2001 and initially developed for privacy-preserving digital signatures. They were later adapted to blockchain technology by the CryptoNote protocol in 2012.
This technique enables transaction anonymity by hiding the sender’s signature among a group of decoy addresses. Thus, the identity of the transaction initiator cannot be directly determined, since the signer appears only as a member of a group. Ring Signatures are one of the core security mechanisms actively used in privacy-focused cryptocurrencies like Monero.
What are Ring Signatures?
Ring Signatures are a type of cryptographic digital signature that allows someone to prove they signed a message while keeping their identity hidden among potential signers.
In traditional digital signatures, a signature is tied to a specific sender. The signature is generated using a private key and verified with the corresponding public key. This system is used to verify that the signed message truly originates from the claimed sender.
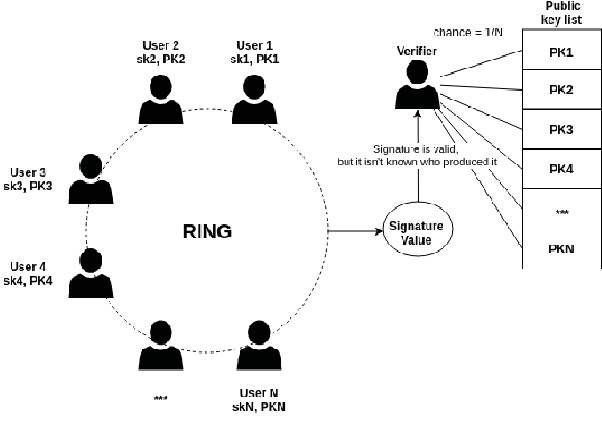
Ring Signatures change this process by hiding the signer’s identity inside a randomly selected group of public keys called a “Ring.” This group includes multiple participants, and externally it is impossible to tell which participant created the signature.
How Do Ring Signatures Work?
Ring Signatures allow the signer to create a verifiable signature without revealing their identity.
To sign a message:
- The signer uses their private key and the group’s public keys to generate a signature.
- The real signer selects a group of public keys including themselves.
- A special mathematical process combines the real signer’s private key with the other public keys.
- The resulting signature is indistinguishable from one created by any group member, but remains valid and verifiable.
Source: Semanticscholar
This ensures that the signature is definitively known to be made by one of the group members, but the actual signer cannot be determined computationally. This property makes Ring Signatures extremely useful for transactions that require anonymity and privacy.Ring Signatures and Blockchain Technology
Public blockchains store all transaction records. Even though data is stored in binary or hexadecimal format, on-chain analysts can track address activity and link senders to recipients. This threatens user privacy and creates a need for a mechanism that maintains transaction anonymity.
Ring Signatures in crypto began with the release of CryptoNote in 2012. CryptoNote is a protocol designed to address certain privacy limitations of Bitcoin. It forms the foundation of privacy-focused cryptocurrencies like Monero and MobileCoin.
Monero
Monero is a privacy-focused, censorship-resistant cryptocurrency known for making transactions extremely difficult to trace. It combines techniques such as Ring Signatures, Stealth Addresses, and Ring Confidential Transactions (RingCT) to achieve privacy.
How Monero Implements Ring Signatures
Monero forms a signing ring by combining the sender’s account keys with several public keys (outputs) from previous users’ transactions.
Through this method:
- In every transaction, the real signer is included in a group.
- Other public keys in the ring hide the real sender from external observers.
- External observers cannot determine which signer executed the transaction.
This makes Monero one of the most private cryptocurrencies, making transaction tracing nearly impossible.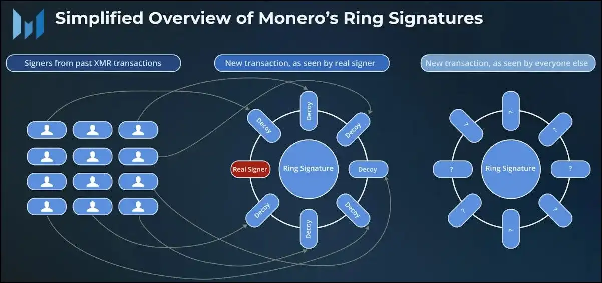
Source: Messari
MobileCoin
MobileCoin is a privacy-focused cryptocurrency operating similarly to Monero. Transactions show that the real input belongs to a larger set, hiding which input is actually used. This process uses the Ring Signature structure.
However, unlike Monero, MobileCoin uses a lighter ring signature implementation to improve efficiency. Thus, MobileCoin transactions confirm faster and require less computational power. This maintains privacy while improving transaction speed.
Alternatives to Consider vs Ring Signatures
Zero-Knowledge Proofs
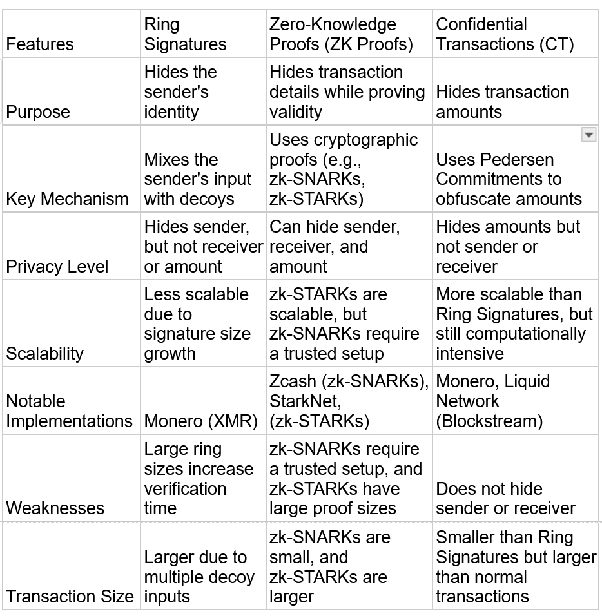
Zero-Knowledge Proofs allow one party to prove a statement is true without revealing additional information. Ring Signatures only hide the sender, while ZK proofs can hide the sender, receiver, and transaction amount simultaneously. This makes ZK proofs more private and secure than Ring Signatures.
Particularly zk-SNARKs produce very small proof sizes, making transactions lighter than Monero’s expanding ring sets. However, implementing ZK proofs is difficult due to cryptographic complexity, high computational cost, and integration challenges. For these reasons, not every blockchain can easily adopt ZK proofs.
Confidential Transactions
Confidential Transactions hide the transaction amount while preserving validity and integrity. It encrypts the transaction amounts using Pedersen Commitments. Thus, nodes verify validity without knowing the actual amount.
Since Confidential Transactions usually only hide the transaction amount, they are combined with other privacy techniques such as stealth addresses or Bulletproofs to provide full anonymity. Ring Signatures obscure the sender, while Confidential Transactions hide the amount. Therefore, both methods can be considered together in different use cases to achieve full privacy.
Comparison: Ring Signatures vs ZK Proofs vs Confidential Transactions
Advantages of Ring Signatures
Privacy
Ring signatures anonymize transactions by protecting the sender’s identity. The transaction input is mixed with decoy data from a larger pool of potential signers. This prevents an observer from identifying which ring member initiated the transaction.
Decentralization
Thanks to decentralization, users can create private transactions using decoys without interacting with any third party. They do not need to directly coordinate with others to form the ring signature group.
Unlinkability
Unlinkability prevents multiple transactions from being linked to the same user even if they sign multiple times. Each transaction generates a new and unique cryptographic signature that does not reveal whether the same private key was used before. This makes Ring Signatures a powerful privacy tool that complicates blockchain transaction tracing.
Disadvantages of Ring Signatures
Higher Computational Costs
Ring signatures involve multiple public keys, making transaction sizes larger. This can cause network congestion and longer confirmation times. Larger transactions often lead to higher transaction fees.
Risk of Misuse
The strong privacy features can make ring signatures an attractive tool for illicit activities. Criminals may prefer privacy-focused cryptocurrencies that use ring signatures to launder illicit funds or purchase illegal goods.
Anonymity Not Guaranteed
Ring signatures enhance privacy but do not provide absolute anonymity. The anonymity level depends on the number of decoys used. If the ring size is small, a sophisticated attacker may identify the true sender.
Regulatory Restrictions
Ring-signature-based assets face growing regulatory pressure. In 2020, the U.S. Secret Service proposed stricter regulations for privacy-focused cryptocurrencies and expressed concerns about their use in illicit activities. Countries such as Japan have banned the trading of privacy-focused cryptocurrencies on regulated exchanges. Such regulatory restrictions may create long-term uncertainty for projects that use ring signatures.
Conclusion
Ring signatures are a cryptographic technology that hides the sender among potential signers, making it difficult to determine who initiated a transaction. This system adds a privacy layer to blockchain transactions, helping users protect their identities.
However, ring signatures also present certain challenges. Because additional data is required to ensure privacy, transactions can become larger, resulting in longer processing times and higher transaction fees. Additionally, the privacy provided by ring signatures carries the risk of being misused for fraud or illicit activity. This situation complicates the balance between privacy and security.
Leading blockchain projects such as Monero and MobileCoin use ring signatures as a core component of their privacy strategies. When combined with other privacy-focused techniques, ring signatures provide a strong and reliable framework for protecting user privacy on the blockchain.
Related Articles

The Legal Journey of Cryptocurrencies in Turkey

Bitcoin İçin Yeni Bir Başlangıç mı? Nubit, Babylon, Bitlayer Çatışması